By Donnie Dong
Cyberspace Administration of China (CAC), the regulator in the field of cybersecurity fined DiDi Global Inc. (DiDi) over RMB 8 billion (US$1.2 billion) on July 21, 2022, for its violation of China’s Cybersecurity Law, Data Security Law and Personal Information Protection Law (PIPL). The CEO and the president of DiDi, being individuals, were also fined RMB 1 million (US$148,000) respectively.
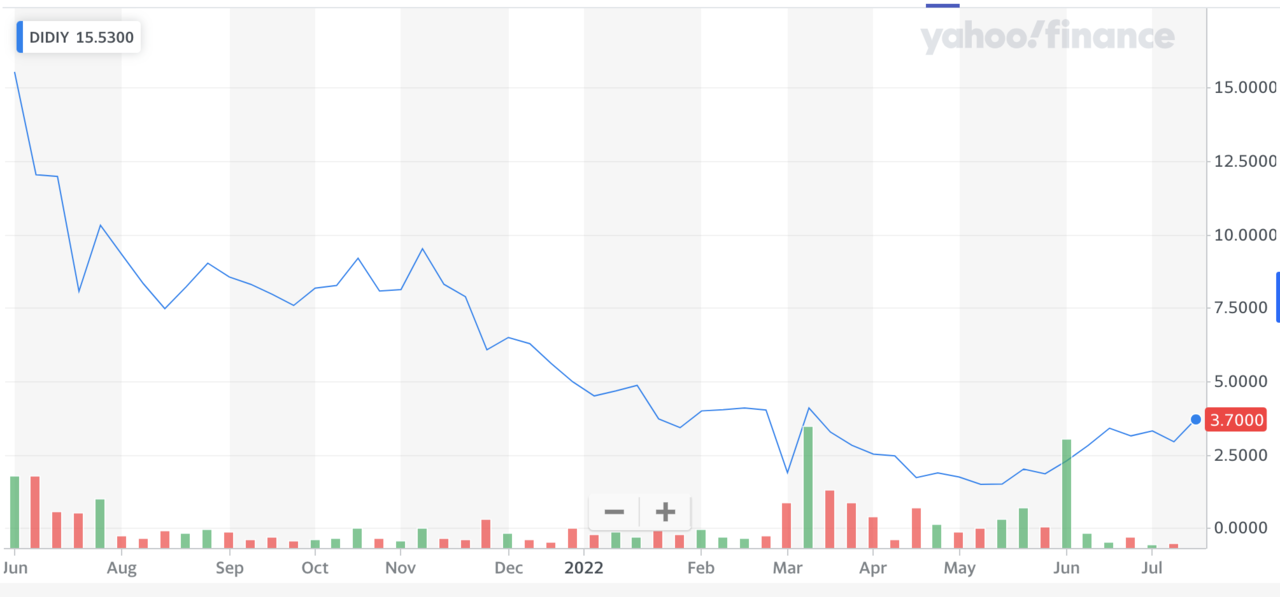
The decision comes over a year after DiDi went public on NYSE on June 30, 2021. CAC launched its “cybersecurity review” against DiDi on July 1, 2021, which was the first case of this sort of enforcement action in China. During the investigation and before the conclusion of the case, CAC has already taken down DiDi’s mobile APPs from various APP stores, which effectively cut off the source of new users. DiDi’s stock price has then slumped throughout the year. The company has announced its plan of delisting from NYSE in May 2022.
CAC did not publish the full text of its decision, citing the reason “national security”. Instead, they announced the above punishments in the form of a news release. According to the limited information disclosed by CAC, DiDi is found to have violated the PRC laws and regulations in the following aspects:
- excessive collection of the passengers’ personal information, including screenshots (stored in the photo albums of the smartphones), passengers’ mobile APP list, passengers’ facial images, geographic information, ages, occupations, and information on personal relationships.
- excessive collection of the drivers’ education backgrounds
- unsecured storage of driver’s PRC resident ID numbers
- analyzing passengers’ travel intentions, permanent location data and travel records without obtaining their express consent
- failure to inform users with the purpose of collecting and processing certain items of personal information.
In its announcement, CAC stated that DiDi’s data processing activities were found endangering national security, while no details were released. Furthermore, DiDi’s reluctance of cooperating with the regulator during CAC’s investigations contributed to the heavy fine, according to CAC.
What should the MNCs learn from the case?
1. The DiDi case shows the Chinese regulator’s increasing scrutiny over data security, personal information processing, and cross-border data transfer. The regulators seemed to have focused their enforcement actions on the following companies/industrial sectors:
- companies who are seeking overseas IPO
- companies who are operating critical information infrastructures
- companies who provide/process credit information
- smart vehicle manufacturers
- developers of popular mobile APPs
2. Personal information protection has been linked to national security, at least for the companies processing a large volume of personal information. In fact, according to a recently promulgated regulation governing the compulsory governmental assessment (and approval) of cross-border data transfer, the CAC has set the following thresholds for launching such assessment when a company:
- is identified (by the government) to be an operator of the critical information infrastructure,
- has processed over 1 million individuals’ personal information
- has provided overseas recipients with over 100,000 individuals’ personal information during the last calendar year, or
- has provided overseas recipients with over 10,000 individuals’ sensitive personal information during the last calendar year.
3. For companies serving individual consumers in China, their privacy policies and user terms must clearly describe the purposes of processing personal data, and their actual data processing activities shall be consistent with the announced purposes.
4. The DiDi case shows that CAC tends to integrate its enforcement powers derived from multiple laws – in the DiDi case, CAC cited provisions from the PRC Cybersecurity Law, Data Security Law, and the PIPL. However, since the case decision was not released, how the laws are applied remains to be unclear.
5. CAC has a broad power of discretions in handling “data security review” investigations. Before concluding the case, they may already order the suspension of the business, closure of websites, or taking down APPs from APP stores. As such, MNCs who have local subsidiaries or presences in China should establish a practical workflow and response plan before they are targeted by the regulators, by working with local counsel or data compliance specialists.
* * * * *
Author: Dr. Donnie Dong is a partner of FuJae Partners, a Certified Information Privacy Manager (IAPP/CIPM), and an Adjunct Professor at the University of Hong Kong’s Academy of Senior Executives. He regularly advises MNCs, unicorns, and start-ups on cross-border intellectual property, data privacy, and related investment and contentious matters.